Camouflage in Gaming
Image courtesy Anne C. Tally.
About the Project
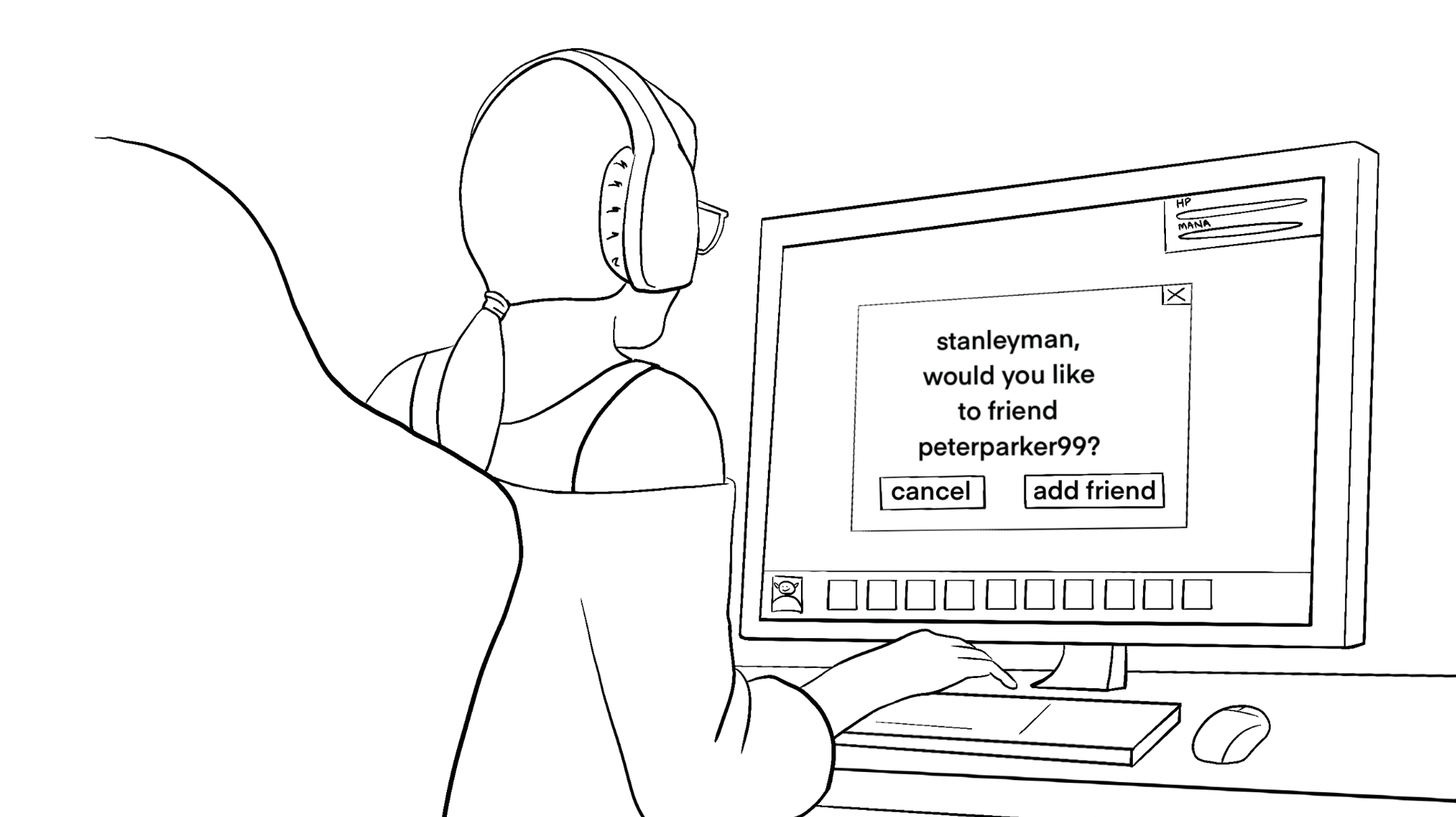
As we seek to protect our privacy and still engage in life on the internet, it has become normal for everyday people to engage in digital deception, too. Amateur online videogame players, for instance, show us just how sensible it can be to disguise oneself during these leisure pursuits. What do you choose to reveal about yourself to friends, family, or strangers in your everyday, online life? How do you try to blend in or stand out in online gaming spaces? We take the novel approach of talking with gamers about the names under which they play to understand more about how individuals negotiate their own desires as well as the technical and social constraints of the game. Ages-old camouflage behaviors can be the key to success.
This project is a collaboration with Katreen Boustani, Yu Ra Kim, and Anne C. Tally.
Publications
Published | Boustani, K., Tally, A. C., Kim, Y. R., & Nippert-Eng, C. (2020, November). Gaming the Name: Player Strategies for Adapting to Name Constraints in Online Videogames. In Proceedings of the Annual Symposium on Computer-Human Interaction in Play (pp. 120-131). DOI: https://doi.org/10.1145/3410404.3414259
Published | Tally, A. C., Kim, Y. R., Boustani, K., & Nippert-Eng, C. (2021, April). Protect and Project: Names, Privacy, and the Boundary Negotiations of Online Video Game Players. Proceedings of the ACM on Human-Computer Interaction, 5(CSCW1), 1-19. DOI: https://doi.org/10.1145/3449233
Third paper in review.
Acknowledgements
We sincerely thank our participants for their time and feedback, which made this research possible. Many thanks also to the anonymous reviewers whose suggestions helped to clarify and strengthen these papers. Thank you to Jacob Abbott, Griffin Halloran, Tianze Huang, Timothy Kelley, Ria Khatana, Oscar Lemus, Emily Meanwell, Serena Patel, Yasmeen Rashidi, and Chandler Shepard for their wonderful advice and contributions as well. Finally, we would like to thank the Department of Informatics at Indiana University, Bloomington for its support.